AWS Academy Cloud Architecting – Module 9 Challenge Lab Questions
View questions in: English
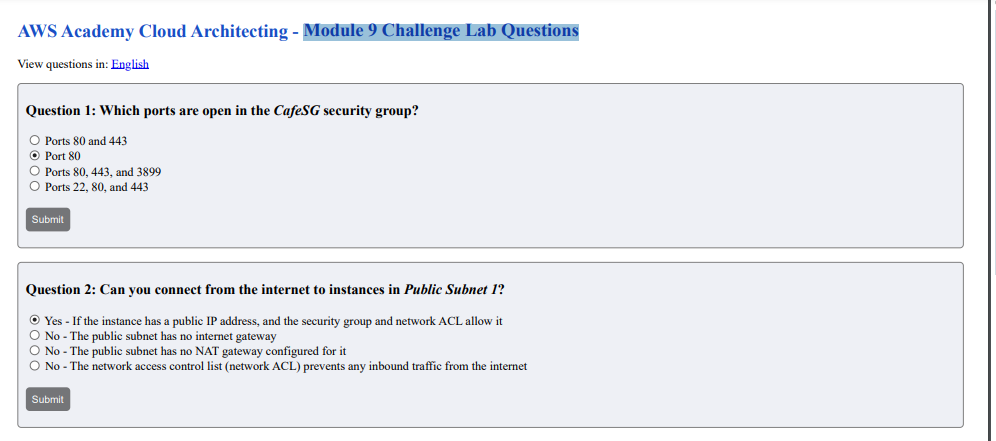
Question 1: Which ports are open in the CafeSG security group?
Top of Form
Ports 80 and 443
Port 80
Ports 80, 443, and 3899
Ports 22, 80, and 443
Bottom of Form
Question 2: Can you connect from the internet to instances in Public Subnet 1?
Top of Form
Yes – If the instance has a public IP address, and the security group and network ACL allow it
No – The public subnet has no internet gateway
No – The public subnet has no NAT gateway configured for it
No – The network access control list (network ACL) prevents any inbound traffic from the internet
Bottom of Form
Question 3: Should an instance in Private Subnet 1 be able to reach the internet?
Top of Form
Yes
No
Bottom of Form
Question 4: Should an instance in Private Subnet 2 be able to reach the internet?
Top of Form
Yes
No
Bottom of Form
Question 5: Can you connect to the CafeWebAppServer instance from the internet?
Top of Form
Yes
No
Bottom of Form
Question 6: What is the name of the Amazon Machine Image (AMI)?
Top of Form
Amazon Linux
WebServerAMI
Cafe WebServer Image
My Amazing Image
Answer Preview: Module 9 Challenge Lab Questions