ITT-116: Project 4: Wide Area Network and Routing
Answer Preview: ITT-116: Project 4: Wide Area Network and Routing
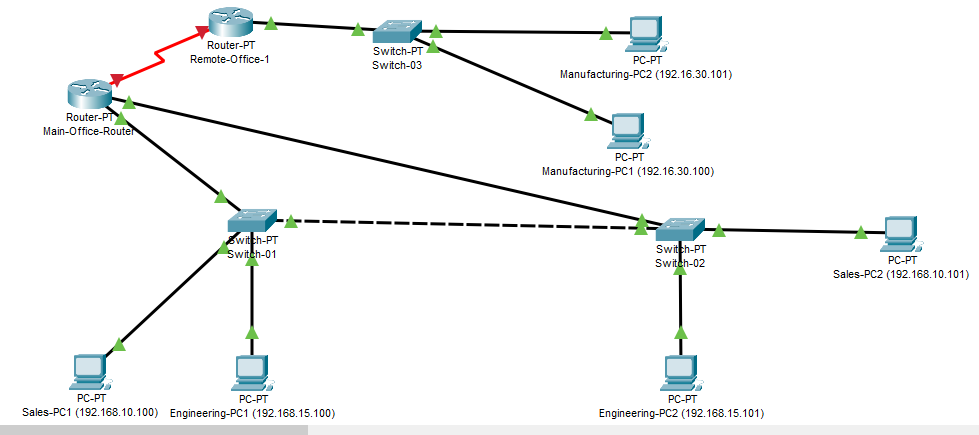
In this activity, you will add layer 3 network routing devices to support connectivity between your local VLANs. You will
add a remote location through a serial connection.
You will continue to build your troubleshooting skills through diagnostics and testing using standard operating system commands.
This activity expands the network you created in the previous topic. Be sure you have completed and tested the network
before starting this activity.
Unless otherwise directed:
• Use the CLI (Command Line Interface) to complete networking device configurations.
• Use the ‘IP Configuration’ tab to configure the PC networking interfaces.
• Use the ‘Command prompt’ to execute troubleshooting commands.
Figure 9 Example Completed Project
Project 4 – Instructions:
Open Packet Tracer.
Load the Project 1 packet tracer file, save the file with a new name.
SAVE your Packet Tracer file as follows:
finitial-lname-section-project-2 i.e. fflintstone-itt116TR100A-project-2
Page 10 of 33
Enable the branch office site:
Figure 10 Remote Office – 01
Add one new Switch-PT device to the diagram.
Reconfigure the interface modules (See Appendix A – Sample devices).
Remove NM-1FGEs from Slots 5 & 6.
Add NM-1CGE to Slot 9.
Label this new switch as ‘Switch-03’..
1. Configure the hostname
2. Disable ip domain-lookup.
Add and connect at least two new PCs to the new switch.
3. Connect one PC to FastEthernet0/1 on Switch-03.
4. Connect one PC to FastEthernet1/1 on Switch-03.
5. Configure Display names ‘Manufacturing-PC1 (192.16.30.100)’.
6. Configure IP addresses on the new PCs.
7. Start with 192.168.30.100, increment by 1.
8. Set the default gateway to 192.168.30.1
9. LEAVE the new switch ‘isolated’ from the other switches.
Add a PT-Router to the workspace and place it near Switch-03 in the diagram.
10. Power off the router.
a. Remove all of the interface modules.
b. Insert one NM-1SS in slot 0.
c. Insert one NM-1CGE in slot 9 and Slot 8.
11. Add a single PT-ROUTER-NM-ICGE module to the router, place it in Slot 0.
12. Add a single PT-ROUTER-NM-1SS module to the router, place it in Slot 9.
(Remember to power it off first!)
NOTE: Slot placement is important!
13. Label the router ‘Remote-Office-1’.
14. Connect the Remote-Office router to Switch-03 using the proper ethernet connection type.
Page 11 of 33
15. Open the CLI interface on Remote-Office-1 router.
a. If prompted: Do NOT enter the initial configuration dialog.
b. Type ‘no’ and press enter, then press enter again to enter user mode.
Configure the Remote-Office Router with the typical administrative items:
16. Set a hostname.
17. Disable IP domain-lookup.
18. Return to privilege mode (End).
19. Show the running configuration. Note the default status of the communication interfaces:
a. gigabitEthernet9/0
b. serial0/0
Are the interfaces enabled?
20. Enter interface configuration mode for GigabitEthernet 9/0.
Set an IP address for the ethernet (LAN) interface:
21. At the config-if prompt:
a. ip address 192.168.30.1 255.255.255.0
b. Enable the interface Hint: no shutdown
22. Using a straight-through cable, connect Interface GigabitEthernet 9/0 on the router to Interface
GigabitEthernet 9/1 on the switch. (Why use a straight-through vs. a cross-over?)
23. Enter interface configuration mode for Serial0/0.
Set an IP address for the serial (WAN) interface:
24. At the config-if prompt:
a. ip address 192.168.255.2 255.255.255.252
b. Enable the interface.
Add Headquarters WAN connectivity:
25. Add a PT-ROUTER router to the ‘main office’ (place it near Switch-01’ in the workspace).
26. Remove All default interface modules.
27. Add a single PT-ROUTER-NM-ISS module to the router, place it in Slot 0.
28. Add two PT-ROUTER-NM-ICGE module to the router, place them in Slots 8 & 9.
29. Label the router ‘Main-Office-Router’.
30. Add slot covers for the remaining slots.
a. Why? Read the description of slot covers
31. Using the proper ethernet cable type, connect GigabitEthernet9/0 on the Main-Office-Router to the
GigabitEthernet8/1 Switch-01.
32. Connect GigabitEthernet8/0 on the Main-Office-Router to GigabitEthernet8/1 on Switch-02.
Configure the Main-Office-Router:
33. Set the hostname and, disable ip domain-lookup
Page 12 of 33
Configure the Main-Office-Router communication interfaces:
34. Enter interface configuration mode for GigabitEthernet9/0.
35. Set an IP address and mask:
a. 192.168.10.1 255.255.255.0
b. Enable the interface.
36. Repeat the previous two steps for Gi8/0, except: Assign IP address 192.168.15.1 to the interface.
37. Enter interface configuration mode for Serial0/0.
a. interface s0/0
38. Set an IP address.
a. ip address 192.168.255.1 255.255.255.252
b. Enable the interface.
39. Using a Serial DCE connector at the Main-Office-Router, Connect Serial0/0 on Main-Office-Router to
Serial0/0 on Remote-Office-One-Router.
On Main office switches Check/verify the trunk configurations in the main office
40. Ensure VLANs 10 and 15 are allowed on the trunk between Switch-01 and Switch-02.
a. (Hint: Show interface trunk)
b. (Test: hint: Ping from one device to the other)
41. On Switch-01:
a. Assign Interface gigabit8/1 to VLAN 10.
42. On Switch-02:
a. Assign Interface gigabit8/1 in VLAN 15.
Add routing to the main and manufacturing routers to enable routing from all networks to all networks
43. On the main office router:
a. Enter global configuration mode.
b. Add a static route to the Remote Office 1 site.
i. ip route 192.168.30.0 255.255.255.0 192.168.255.2
44. On the Remote Office 1 router:
a. Enter global configuration mode.
b. Add static routes for the Main office site.
i. ip route 192.168.10.0 255.255.255.0 192.168.255.1
ii. ip route 192.168.15.0 255.255.255.0 192.168.255.1
Page 13 of 33
SAVE your running configurations on all devices.
Test your network connectivity.
Ping from each PC in Remote Office to PCs in Main office.
Ping from each PC in Main office to PCs in Main office AND PCs in Remote.
Do they all work?
Troubleshoot and correct as needed.
SAVE ALL RUNNING CONFIGURATIONS on ALL ROUTERS and SWITCHES.
SAVE YOUR PACKET TRACER FILE.
PRACTICE:
SHOW RUNNINNG CONFIGURATIONS
SHOW TRUNK settings on Switches
SHOW VLAN configurations on switches
SHOW IP ROUTING on Routers
TEST DIFFERENT PING and TRACEROUTES to test your networks
APPLY TROUBLESHOOTING TECHNIQUES:
SPLIT the problem
IDENTIFY Trunk, VLAN, and IP Address mis-matches
Project 4 – Scoring (30 points total):
Install and configure Routers with correct interface modules: 10 points
Configure Router interface IP addressing: 5 points
Configure new Switch interfaces, PCs, addressing: 5 points
Configure IP Routing: 5 points
Network functions properly: 5 points
Page 14 of 33
Project 4 – Complete and submit your work
SAVE your Packet Tracer file as follows:
finitial-lname-section-project-4 i.e., fflintstone-itt116TR100A-project-4
ZIP the file – keep the name intact. i.e., fflintstone-itt116TR100A-project-4.zip
SUBMIT the completed packet tracer file as a ZIPPED file to the assignment page in the digital classroom.
Screenshots are not acceptable.
Project 5: IP Subnetting, Future Proofing, Expanding, Opt