Exploitation Quiz-Attempt History
| Attempt | Time | Score | |
| LATEST | Attempt 1 | 10 minutes | 8 out of 10 |
Submitted Jun 23 at 3:48pm
This attempt took 10 minutes.
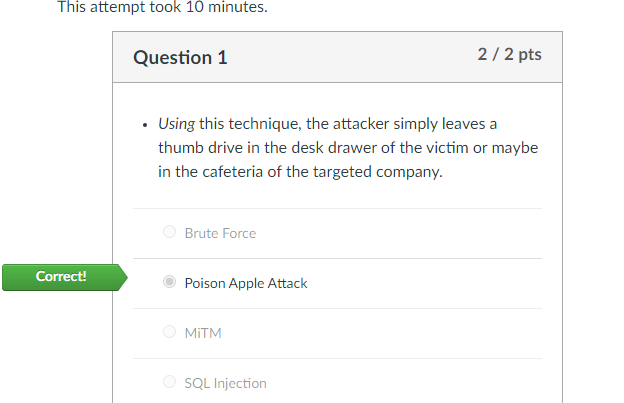
Question 1
Using this technique, the attacker simply leaves a thumb drive in the desk drawer of the victim or maybe in the cafeteria of the targeted company.
Brute Force
Poison Apple Attack
MiTM
SQL Injection
Question 2
Can travel from system to system without human interaction
Virus
Spyware
Trojan
Worm
Question 3
Rewrites itself every time it infects a new file.
Polymorphic virus
Metamorphic virus
Boot trap virus
Master Boot Record
Question 4
Infect files by placing their code at the end of the infected file. This leaves the file intact, with the malicious code just added to the beginning or end of the file.
Appenders
Prependers
Offenders
Defender
Question 5
Intercepts a virus when it starts to execute and blocks it from infecting other programs or data.
Activity blocker
Execute blocker
Domain executer
Virus blocker
Answer Preview-Exploitation Quiz FIVE-INT-268