CMIT 495 Cybersecurity Technology Capstone Syllabus
- CMIT 495
- Fall 2023
- Section 6384
- 3 Credits
- 08/16/2023 to 10/10/2023
Faculty Contact
Brian Nelson [email protected]
Course Description
Prerequisites: Completion of at least 27 credits of CMIT coursework. A comprehensive project-driven study of network design and security, with an emphasis on the integration of knowledge, practical applications, and critical thinking. The objective is to implement a secure and scalable network to meet organizational needs. Topics include advanced concepts in network and security design.
Course Introduction
This course is a project-driven study of trends in computer networks and cybersecurity, with emphasis on the integration of knowledge, practical application, and critical thinking. Each week,you will explore a new topic and consider how the technology or concept may be applied or implemented to provide value-added benefit in the scenario provided. By the completion of this course, you will have an understanding of virtualization, cloud computing, software-defined networking (SDN), machine learning and data analytics, and current cybersecurity strategy, law, and policy.
You will also develop and use effective collaboration skills to include communication, compromise, tolerance, and reliability. These skills will enable successful outcomes for the team-based projects.
The concepts learned and applied in this course will be directly applicable to a career in computer networks and cybersecurity.
Course Outcomes
Course outcomes are phrased in the form of learning goals. After completing this course, you should be able to
- Communicate effectively in a variety of contexts.
- Evaluate complex problems.
- Apply quantitative skills to analyze data and solve problems.
- Collaborate toward a common purpose.
- Develop job-seeking skills.
- Install, administer, and configure systems and networks in physical, virtual, and cloud environments to support an organization’s needs.
- Apply industry best practices to resolve information technology problems and meet the needs of the management team, staff, and end users
- Protect client data by maintaining confidentiality, integrity, and availability (CIA) in order to meet organizational objectives.
- Apply effective workforce skills, best practices, and ethical principles in completing information technology tasks within an organization.
Course Materials
Click to access your course materials information
Class Guidelines
Students With Questions or Concerns
If you have questions related to the course content or any of the graded deliverables, contact the instructor.
Contacting Advising or the Department
- If you have questions related to the course content or any of the graded deliverables, please contact your instructor.
- For questions and concerns related to advising, you can call 800-888-8682 (toll-free), or, write to [email protected].
- For other questions and concerns about this class, you can contact your program director by writing to [email protected] . Please be sure to mention the course name, course number, and your section number in the “Subject:” field of your email. Your email will be treated confidentially.
Use of TurnItIn
All CMIT courses and sections are now using TurnItIn to check student projects for originality. See the TurnItIn section under Academic Policies (in this syllabus) for more information about the TurnItIn Originality Checking Service.
See the announcement titled “Use of TurnItIn” for specific information pertaining to TurnItIn use in this class.
If you wish to not have your paper stored in Turnitin, you must notify your instructor within the first two weeks of the course.
Grading Information
This course consists of the following graded items:
| Week 1 – Virtualization Assignment | 12% |
| Week 2 – Cloud Computing Assignment | 12% |
| Week 3 & 4 – SDN & IBN Individual Paper | 20% |
| Week 5 & 6 – The Cybersecurity Threat Landscape Team Project | 25% |
| Week 7 & 8 – Cybersecurity Strategy, Law and Policy Team Paper | 25% |
| Discussion 1: Communicating Your Qualifications Using CareerQuest | 2% |
| Discussion 2: Networking and Employment Opportunities | 2% |
| Discussion 3: What Is Your Target Job? | 2% |
| Total | 100% |
This class uses a standard method of rounding final grade (not individual assignment grades). If your grade ends in 9.5 or above and is on the cusp of a letter grade, you will receive the higher letter grade. If it ends in 9.4 or below it will be the lower letter grade.
Attendance and Participation
By registering for a course, whether on onsite, online or hybrid, you have made a commitment to participate in class discussions and activities. Plan to participate regularly. In this course, there are three discussions relating to careers in the computer networking and cybersecurity field. Since these discussions are about career development, you are encouraged to participate early and often to gain the most from the activity, but no later than the week they are assigned to receive credit.
Assignment Re-submissions
In order to allow you to get credit for your best work, this course features the following policies for re-submission of graded work after you receive instructor feedback on assignments:
- Written Assignments
You are allowed one re-submission for each assignment provided the original grade from the instructor was a B or less.The re-submission is due within one week of receiving graded faculty feedback. It is your responsibility to ensure that the re-submission is turned in within a week of receiving faculty feedback and to alert your instructor that an assignment has been re-submitted and should be reviewed again.
- Teamwork Assignments
You may re-submit the individual portion of teamwork assignments that receive a grade of B or less within one week of receiving graded faculty feedback. Only one re-submission per assignment is allowed. There is no revision of the team evaluation allowed.
- Discussions
No re-submissions are allowed.
Late Policy
- Written Assignments
You may submit work up to one week after the posted deadline without penalty. Work submitted after this will lose 5 percent per day. Re-submissions do not have a grace period and must be submitted within one week of receiving faculty feedback. Work submitted after the grace period (original submissions) or one week following faculty feedback (re-submissions) will lose 5 percent per day late. If you submit work late, any penalty still applies even if you resubmit the work to improve your grade.
- Teamwork Assignments
You may submit work up to one week after the posted deadline without penalty on the individual portion, but the team evaluation will be based on timely team participation up to the due date. Re-submissions do not have a grace period and must be submitted within one week of receiving faculty feedback. Work submitted after the grace period (original submissions) or one week following faculty feedback (re-submissions) will lose 5 percent per day late. If you submit work late, any penalty still applies even if you resubmit the work to improve your grade.
- Discussions
Discussions are due the week they are assigned in class; late submissions will not receive credit.
Extra Credit
Extra credit is not available.
Project Descriptions
Projects
You will be given individual and team-based projects that will require you to provide network and security solutions in a team environment. The specific application of concepts learned in the major thus far will be necessary for a successful outcome.
The assignments must be completed individually and as a group (assigned during the first week of class). The assignments are modular, correspond to the weekly content topic, and include:
| Week | Project | Type | Submissions | Deliverables |
| 1 | Virtualization Assignment | Individual | Individual | Linux-based VM (Proof of Concept) using AWSeducate |
| 2 | Cloud Computing Assignment | Individual | Individual | Extend Project 1 using Cloud-based (AWS) cloud infrastructure (IaaS) by installing and configuring a Microsoft Windows operating system (PaaS) that can be accessed on demand by any end-user device. |
| 3 & 4 | Software-Defined Networking (SDN) & Intent-Based Networking (IBN) | Group | Individual with group collaboration | Minimum length 5- to 6-page White Paper for the CTO |
| 5 & 6 | The Cybersecurity Threat | Group | 1 submission for the group; all members submit a peer review worksheet | Minimum length 10- to 15-page analysis for the CTO |
| 7 & 8 | Cybersecurity Strategy and Policy | Group | 1 submission for the group; all members submit a peer review worksheet | Minimum length 10- to 15-page paper for the CTO |
Week 1: Virtualization Assignment
In this assignment, you will use the Amazon Web Service (AWS) to install and configure a Linux virtual machine and create a working proof of concept (PoC). Use the assignment template provided to document your progress, embed the appropriate screenshots, and answer questions related to the scenario.
Week 2: Cloud Computing Assignment
In this assignment, you will use Amazon Web Services (AWS) infrastructure as a service (IaaS) to deploy a cloud-based platform as a service (PaaS), working with Microsoft Windows operating systems. You will use the assignment template provided to document their progress, embed the appropriate screenshots, and answer questions related to the scenario.
Week 3 & 4: Software Defined Networking (SDN) & Intent-Based Networking (IBN) Individual Paper
In this assignment, you will submit a white paper that introduces the concepts and architecture of SDN/IBN, the pros and cons of each, and how virtualizing the desktop and back-end infrastructure are complementary and related. You will also be introduced to your team and brainstorm ideas for this assignment. While collaboration is expected, the final deliverable will be an individual minimum 5- to 6-page white paper from each student that discusses the benefits of SDN/IBN.
Week 5 & 6: The Cybersecurity Threat Group Project
In this assignment, you will work in a team to analyze an advanced persistent threat (APT) to an organization, while applying machine learning and advanced data analytic principles as a cybersecurity solution. The final deliverable will be a minimum 10- to 15-page paper that covers threat landscape analysis; APT analysis; cybersecurity tools, tactics, and procedures; machine learning and data analytics; and using machine learning and data analytics to prevent APT.
Week 7 & 8: Cybersecurity Strategy and Policy Group Paper
In this assignment, you to work in a team to analyze the US national cybersecurity strategy, law, and policy, or lack thereof; and propose a solution that is most conducive to enabling a secure internet. The final deliverable will be a minimum 10- to 15-page paper that covers national security strategy and cybersecurity; partnerships between public and private sector organizations; protecting the US homeland, and an exploration of cybersecurity technologies.
Discussions
There are discussions in this course. Discussions in the online classroom are similar to discussions in real life. They are an exchange of ideas. Discussions in the CMIT courses are structured group activities that require collaboration and teamwork between students.
Academic Policies
ACADEMIC INTEGRITY
University of Maryland Global Campus (UMGC) has adopted a Philosophy of Academic Integrity to guide the university’s commitment to a culture of academic integrity. Our approach cultivates socially responsible personal and professional behaviors and traits. All members of the University community must maintain the highest level of integrity across the academic experience.
Resources – UMGC provides an Academic Integrity Tutorial and an Integrity & Ethics Badge as learning resources. These resources include information on the fundamentals of academic integrity and how to apply your own personal ethics to coursework as a UMGC student and in other settings. Other Academic Integrity resources and guidelines are found at https://www.umgc.edu/current-students/learning-resources/academic-integrity.
Role of Instructor – Your instructor is your primary resource for how to uphold the highest ethical standards in the context of the specific requirements for this course.
Student Responsibility – You are responsible for using UMGC-approved resources to understand key academic integrity concepts and to support your own academic success through practices that uphold values of integrity: honesty, trust, fairness, respect, responsibility, and courage.
Turnitin – Turnitin is enabled within the classroom to support the development and assessment of authentic student writing. To learn more about Turnitin, the feedback it provides, how to use that feedback to improve your work, and your options regarding the inclusion of your work in the Turnitin database, visit University guides for Turnitin at https://libguides.umgc.edu/turnitin-faq.
CLASSROOM CIVILITY
University of Maryland Global Campus is committed to the success of our global community and values the diverse identities and backgrounds of our students, faculty, and staff. Each one of us has a broader life and set of experiences beyond UMGC that we bring with us to each interaction. Sharing your story with your classmates provides opportunities to learn, relate, and gain inspiration from each other. Engagement often begins with introductions at the beginning of the course. Sharing your preferred name, preferred pronouns, and other details about yourself and your life builds a foundation for connection, understanding, and a richer and more personalized learning experience.
We also recognize that some of life’s responsibilities and challenges outside of the classroom, such as childcare, a change in employment status, or illness, have an impact on success in a course. To the extent you are comfortable, we encourage you to communicate with your faculty member or Success Coach about any concerns you have for this course or as a student at UMGC so we can help you navigate potential obstacles and stay on track to achieve your goals.
Students are expected to work together cooperatively, and treat fellow students and faculty with respect, showing professionalism and courtesy in all interactions. Please review the Code of Civility for more guidance on interacting in UMGC classrooms: https://www.umgc.edu/current-students/student-life-and-support/student-handbook/civility-code.
POLICIES AND GUIDELINES
UMGC is committed to creating a climate in which everyone can thrive. UMGC’s Non-Discrimination and Anti-Harassment Policy (Policy VI-1.00) and Sexual Misconduct Policy (Policy 041.00) protect students, faculty, and staff.
Here you will find UMGC’s Non-Discrimination Statement.
Students with disabilities who need accommodations in a course are encouraged to contact the Office of Accessibility Services (OAS) at [email protected], or call 240-684-2287.
The following academic policies and procedures apply to this course and your studies at UMGC.
| 150.25 | Academic Integrity Policy The University expects all members of the university community—students, faculty, and staff—to use guidelines to work with and promote integrity. If you are aware of any academic misconduct, please contact [email protected]. All cases of academic misconduct will be addressed in accordance with Policy 150.25 and associated procedures.You are expected to engage in new learning that furthers your development of knowledge, skills, and abilities in each course. According to this policy, you may not submit a substantial portion of any coursework that you have submitted to any course previously without express written approval through assignment guidelines or other forms of communication. You must use UMGC course materials responsibly. Uploading course materials to any website outside of UMGC’s online classroom is prohibited by this policy. |
| V-1.03 | Code of Student Conduct |
| 170.40170.41170.42 | The following policies describe the requirements for the award of each degree: Degree Completion Requirements for Graduate StudentsDegree Completion Requirements for a Bachelor’s DegreeDegree Completion Requirements for an Associate’s Degree |
| V-1.30 | Student Reasonable Accommodation Policy – Students are responsible for self-identifying with Accessibility Services to inform the university about medical conditions and request academic accommodations. |
| 170.71 | Policy on Grade of Incomplete – Additionally, the mark of I depends on the following two criteria: Students who have completed 60% of their coursework with a grade of B or better for graduate courses or C or better for undergraduate courses and students who request an I before the end of the term. The mark of I is not available for noncredit courses. |
| 170.72 | Course Withdrawal Policy – Students must follow drop and withdrawal procedures and deadlines available at https://www.umgc.edu/admission/academic-calendar under Academic Calendar. |
| 130.80 | Procedures for Review of Alleged Arbitrary and Capricious Grading – Appeals may be made on final course grades as described herein. |
| IV-3.20 | Intellectual Property – All university faculty, staff, and students must comply with University guidelines on the use of copyrighted material. Uploading UMGC or faculty copyrighted material without authorization degrades and corrupts the integrity of the teaching and learning experience and is a potential violation of UMGC policy and copyright law. You must obtain permission to post UMGC or other’s copyrighted material to third-party websites, including social learning network sites. UMGC reserves the right to take appropriate action to remove copyrighted material uploaded without authorization. |
| 205.06 | Calculation Of Grade-Point Average (GPA) for Inclusion on Transcripts and Transcript Requests – Note: Undergraduate and graduate courses have different Grading Policies. See the Grading Policies section of the Course Syllabus. |
| X-1.12 | Acceptable Use – The security of the online classroom is critical to ensuring a strong culture of academic integrity and authentic education at the University. It is a violation of the University’s policies for anyone to share logon, password, and any other secure information about a UMGC online account, including credentials required to access the online learning environment. |
GRADING
According to UMGC’s grading policy, the following marks are used:
| Undergraduate | Graduate | |
| A | 90-100% | 90-100% |
| B | 80-89% | 80-89% |
| C | 70-79% | 70-79%* |
| D | 60-69% | N/A** |
| F | 59% or below | 69% or below |
| FN | Failure-Non attendance | Failure-Non attendance |
| G | Grade Pending | Grade Pending |
| P | Passing | Passing |
| S | Satisfactory | Satisfactory |
| U | Unsatisfactory | Unsatisfactory |
| I | Incomplete | Incomplete |
| AU | Audit | Audit |
| W | Withdrew | Withdrew |
* The grade of “B” represents the benchmark for graduate courses. Students must maintain a Grade Point Average (GPA) of 3.0 or higher. Classes where final grade of C or F places a student on Academic Probation must be repeated.
** UMGC does not award the grade of D in graduate courses.
GRADE ROUNDING
Scores to individual assignments are calculated based on rubrics in the class and are not rounded to the whole point. The final grade for the course is determined by weighted average and will be rounded to the nearest whole point using mathematical rule (grades with .5 and above to be rounded to the next whole point).
EXTRA CREDIT
Assignments are designed to enable students to achieve course objectives and succeed in the program. In the interest of equity and fairness, there will be no extra credit opportunities. All assignments are identified in the syllabus.
COURSE EVALUATION SURVEY
UMGC values its students’ feedback. You will be asked to complete an online evaluation toward the end of the term. The primary purpose of this evaluation process is to assess the effectiveness of classroom instruction in order to provide the best learning experience possible and make continuous improvements to every class. Responses are kept confidential. Please take full advantage of this opportunity to provide your feedback.
LIBRARY SUPPORT
Extensive library resources and services are available online, 24 hours a day, seven days a week at https://libguides.umgc.edu/home to support you in your studies. The UMGC Library provides research assistance in creating search strategies, selecting relevant databases, and evaluating and citing resources in a variety of formats via its Ask a Librarian service.
EXTERNAL LINK DISCLAIMER
This course may contain links to external sites neither owned nor maintained by UMGC. UMGC bears no responsibility for the accuracy, legality, or content of external sites or for that of subsequent links. In addition, the terms of use, security policies, and privacy policies may differ from those of UMGC. Contact the external site for answers to questions regarding its content, terms of use, and policies.
LEARNING MANAGEMENT SYSTEM SUPPORT
Those requiring technical assistance can access Help@UMGC Support directly in LEO under the Help menu. Additional technical support is available 24 hours a day, seven days a week via self-help and live chat at https://www.umgc.edu/help or by phone toll-free at 888-360-8682.
SYLLABUS CHANGES
All items on this syllabus are subject to change at the discretion of the Instructor and the Office of Academic Affairs.
Class & Assignment Schedule
| Week | Assignments |
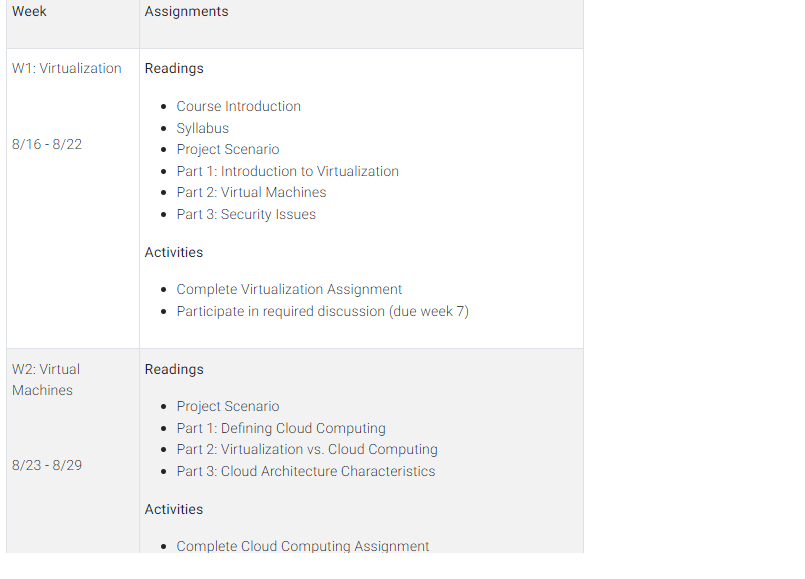
| W1: Virtualization 8/16 – 8/22 | ReadingsCourse IntroductionSyllabusProject ScenarioPart 1: Introduction to VirtualizationPart 2: Virtual MachinesPart 3: Security IssuesActivitiesComplete Virtualization AssignmentParticipate in required discussion (due week 7) |
| W2: Virtual Machines 8/23 – 8/29 | ReadingsProject ScenarioPart 1: Defining Cloud ComputingPart 2: Virtualization vs. Cloud ComputingPart 3: Cloud Architecture CharacteristicsActivitiesComplete Cloud Computing Assignment |
| W3: Software-Defined Networking (SDN)8/30 – 9/5 | ReadingsProject ScenarioPart 1: Introduction to Software-Defined NetworkingPart 2: Security IssuesActivitiesBegin SDN and IBN Paper |
| W4: Intent-Based Networking (IBN) 9/6 -9/12 | ReadingsProject ScenarioPart 1: Overview of Intent-Based NetworkingPart 2: IBN and SDNActivitiesComplete SDN and IBN Paper |
| W5: The Cybersecurity Threat Landscape9/13 – 9/19 | ReadingsProject ScenarioPart 1: Cybersecurity IssuesActivitiesBegin Cybersecurity Threat Landscape Team Project |
| W6: Machine Learning and Data Analytics for Cybersecurity 9/20 – 9/26 | ReadingsProject ScenarioPart 1: Overview of Machine LearningPart 2: Data and Data Analytics for Machine LearningActivitiesComplete Cybersecurity Threat Landscape Team ProjectSubmit Peer Review Form to Instructor |
| W7: Cybersecurity Strategy, Law and Policy 9/27 – 10/3 | ReadingsProject ScenarioPart 1: Cybersecurity StrategyPart 2: Cybersecurity PolicyActivitiesBegin Cybersecurity Strategy, Policy, and Law Team PaperParticipate in the required discussions |
| W8: Blockchain 10/4 – 10/10 | ReadingsProject ScenarioPart 1: BlockchainActivitiesComplete Cybersecurity Strategy, Policy, and Law Team PaperSubmit Peer Review Form to Instructor |

Leave a Reply