Firewalls & IDS Quiz EIGHT-
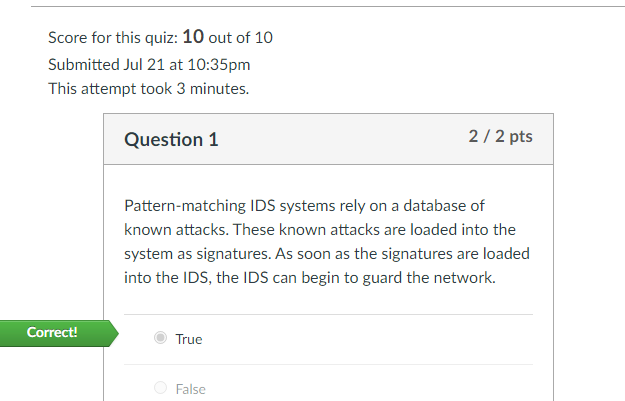
Question 1
Pattern-matching IDS systems rely on a database of known attacks. These known attacks are loaded into the system as signatures. As soon as the signatures are loaded into the IDS, the IDS can begin to guard the network.
True
False
Question 2
Anomaly detection is good at spotting behavior that greatly differs from normal activity
True
False
Question 3
Firewalls are hardware or software devices designed to limit or filter traffic between a trusted and untrusted networkct!
True
False
Question 4
Bastion Host – a server that is highly locked down (hardened). Usually put in a DMZ.Correct!
True
False
Question 5
A DMZ is a protected network that sits between the untrusted Internet and the trusted internal network. Servers deployed in the DMZ need to be hardened and made more secure than the average internal computer. These systems are called bastion hosts.
True
False
Answer Preview-Firewalls & IDS Quiz EIGHT-INT-2681