CST 630 Project 1: Reconnaissance
-
QUESTIONS: Based on your experience analyzing the report and identifying potential threats based on the threat description, propose mitigation, update the justification field, and answer the following questions. Your answers should be added to the PTPR in the Appendix with an appropriate heading.
- Identify at least 3 threats that are not applicable to your model and explain why.
- Are there any threats that you have identified manually that the model does not include? 3. Identify at least two and explain why this is so. Also, what does this tell you about the capacity of the MTMT?
- Which element/device is reported to have the most vulnerabilities in your report?
- Which element/devices is reported to be the most secure from the threat report?
-
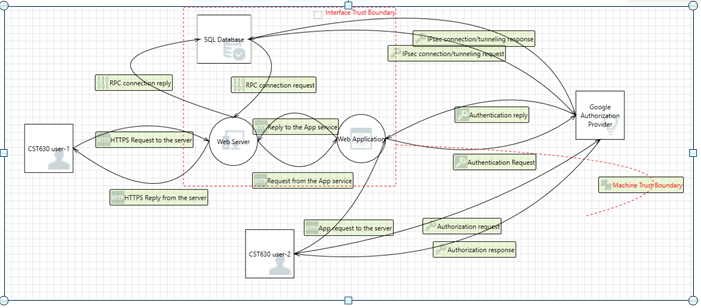
Insert the DFD into section 3.3 of the PTPR and use the information populate section 3.4 per the instructions in the report.
-
Information Gathering (To be completed within MARS)
Use your Recon folder in the web browser to find the 4 sites listed above. Use common search engines (different ones from the ones used from the OSINT framework) to search for information on the websites.
- What type of public information can you gather that may help you perform penetration testing if you were a malicious user?
- URL
- Account Remember Me
- Social media is best way to gather information – chirpyhub followers seem to be other Cyberapolis businesses so maybe they are interconnected and if one has a backdoor, that could a malicious actor to the bank’s network, also the followers could also be employees, so taking their names and trying to brute force accounts, it also shows PII (email addresses and phone numbers, you can launch other attacks with this information).
- It shows the address, phone number, and the service numbers you can tell are automated because they are 24/7. If you can gather customer’s information a malicious user may use it to gather information from the automated system
- With emails you can send phishing emails
- What are some strengths of the website?
- you have to be a user to login
- you cannot create your own account
- if invalid credentials the error message only gives the least amount of information
- What are some weaknesses of the website?
- the invalid login threshold is not set
- no input validation on services and contact us page when entering private information
- Does the source code reveal any information to you?
Answer Preview: Project 1: Reconnaissance
$40.00
